How ICE Will Spy On Protesters, And How You Can Protect Your Privacy
Jake Laperruque / Feb 11, 2026Jake Laperruque is a Tech Policy Press Fellow and the Deputy Director of Security & Surveillance at the Center for Democracy & Technology. This piece is written in his personal capacity for the fellowship and does not necessarily reflect the views or positions of his employer.

A corrections officer walks beside people holding candles, signs, and flowers during a vigil outside the Krome Detention Center in Miami on May 24, 2025, protesting US Immigration and Customs Enforcement custody and mass deportations. (Photo by GIORGIO VIERA/AFP via Getty Images)
The killing of Renee Nicole Good and Alex Pretti by federal agents in Minneapolis last month seemed to mark a breaking point for the United States on immigration enforcement. But rather than lowering tensions, the government appears intent on cranking the temperature up. President Donald Trump framed Good’s killing as the price of being “disrespectful of law enforcement” and described Pretti as an "agitator" and “insurrectionist.” White House Deputy Chief of Staff Stephen Miller described Pretti as a “domestic terrorist” and “would-be assassin" (claims Vice President Vance amplified) while labeling broader protests as an “insurgency.”
The administration isn’t just criticizing anti-ICE protesters and observers; it is treating their conduct as criminal. Department of Homeland Security (DHS) Secretary Kristi Noem has claimed that merely filming ICE agents constitutes an act of violence, despite the fact that filming police is not only legal, it is a constitutionally protected right. DHS Assistant Secretary for Public Affairs Tricia McLaughlin has labeled recording ICE personnel as “doxing” subject to prosecution, while a DHS statement described filming agents as "obstruction of justice,” threatening that “we will hunt you down and you will be prosecuted.” Border Patrol commander Greg Bovino, who was removed from his position following Pretti’s killing, has said protesters could be arrested for making “hyperbolic” comments about immigration officers. A DHS bulletin to personnel lists “use of cameras,” “livestreaming,” and filming agents among “unlawful civil unrest” tactics.
These are not idle threats: As the Cato Institute’s David J. Bier has documented, there is a growing trend of ICE and Border Patrol agents threatening observers who film them with arrest for illegally “impeding” operations. Over the last month, the Department of Justice pushed efforts to investigate Good’s widow for activist ties and launched a criminal probe against Minnesota Governor Tim Walz and Minneapolis Mayor Jacob Frey, both Democrats, for criticizing ICE operations.
Americans should brace for broader investigation and persecution of those who document and criticize immigration enforcement, fueled by an array of powerful surveillance technologies and tools. But they can also take actions to protect their privacy rights.
Electronic location tracking
One of the most powerful tools DHS and its subsidiary agencies can use to monitor protesters and observers is electronic location tracking, achieved by collecting individuals’ phone location data at mass scale. A recent 404 Media report outlined in stark detail how invasive the tools ICE uses for monitoring phone location data can be:
Users can perform a single perimeter analysis to search a specific area for mobile phones across a certain time period …. Users can click a route feature which shows the path the device took …. The software can also do a multi-permiter analysis, which monitors multiple locations at once to see which devices have been present at two or more specific places.
At the push of a button, ICE can catalog individuals who marched in a protest or gathered on a street corner to observe officers' activities and build lists of activists by querying which phones are present at multiple events of interest. Once ICE identifies a person of interest, personnel can use this surveillance tool to track that individual's movements over extended periods, following them to their home, work, and any sensitive locations they visit.
How is such an invasive system legal? The Supreme Court has ruled that cellphone location tracking requires a warrant, and Congress banned domestic bulk collection over a decade ago. Yet DHS agencies circumvent these rules by exploiting the Data Broker Loophole. Rather than obtaining cell phone location data through a formal legal process, they simply buy it in bulk from data brokers like Venntel, Babel Street, and Penlink.
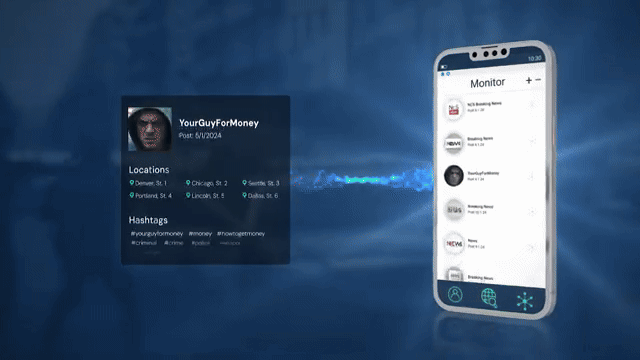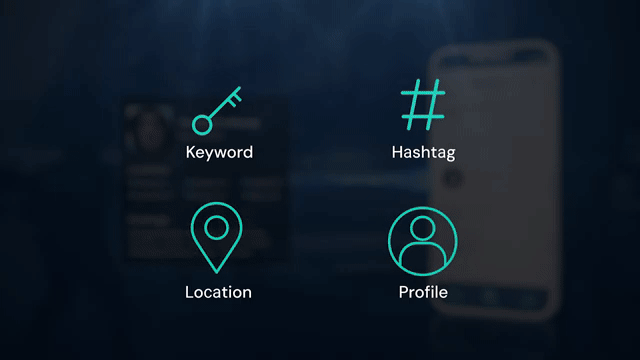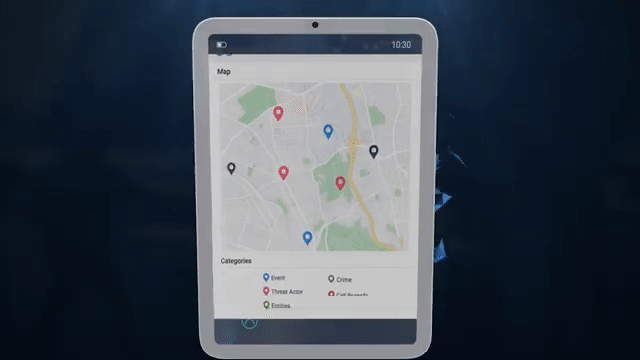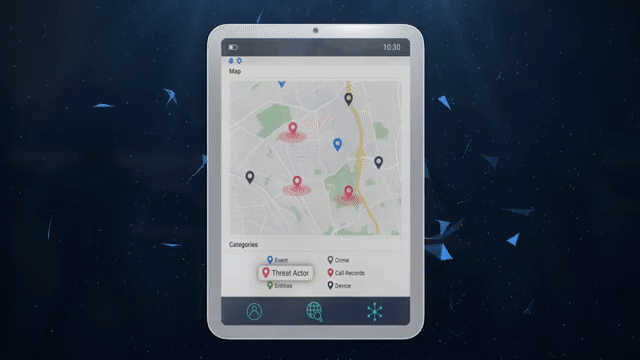
Clip from promotional video by ICE data broker Penlink highlighting its location tracking capabilities.
In effect, Americans’ tax dollars are being used by ICE and CBP to buy their way around the rules and limits on location tracking, facilitating pervasive surveillance and abuse.
Fortunately, this is one area where fixing the law is not only possible, but was recently close to being achieved. Over the past several years, lawmakers—led by Sen. Ron Wyden (D-OR), Sen. Rand Paul (R-KY), Rep. Warren Davidson (R-OH), and Rep. Zoe Lofgren (D-CA)—have advanced The Fourth Amendment Is Not For Sale Act. This legislation would close the Data Broker Loophole and stop law enforcement agencies, including ICE, from purchasing cellphone location data and other sensitive records. This bill came close to passage last Congress—the House of Representatives passed it in 2024, but it failed in the Senate. But there’s a good chance it will come up again as early as this spring, when Congress takes up surveillance reforms ahead of the expiration of part of the Foreign Intelligence Surveillance Act.
Notably, many Democratic lawmakers, now incensed by ICE’s conduct, recently provided decisive votes against these reforms. During the 2024 votes, a slim majority of House Democrats opposed the bill, and most Senate Democrats voted against it. Had all Senate Democrats voted in support, ICE could already be banned from purchasing cell phone data and cut off from these dangerous location-tracking powers. If this measure does come before Congress again this year, activists and constituents have the opportunity to make clear to their representatives that a vote against closing the Data Broker Loophole is a vote for unchecked ICE surveillance and location tracking.
Until the law is fixed, individuals can also take personal steps to protect themselves. There are straightforward ways to prevent cell phone location tracking, but it's important to know what remedies are effective. Switching your phone to airplane mode shuts off the cell signal, but it doesn’t prevent location data from being generated through GPS, meaning apps can still log your location (and potentially sell that information to data brokers, who in turn sell it to DHS). Powering a phone off more effectively blocks location data generation, though even this carries some risk, as many modern phones may still connect via Bluetooth while off. The most reliable privacy measures are to place a phone in a quality-vetted Faraday bag or to leave it at home entirely when attending a sensitive event.
Facial recognition
ICE has for years used facial recognition for immigration enforcement, but over the past year, the agency has dramatically escalated how it uses this biometric surveillance tool. In 2025, ICE began, for the first time, deploying facial recognition for in-the-field identifications, using an app called Mobile Fortify to photograph individuals and run facial recognition scans through their phones.
Field use of facial recognition raises serious risks, as variable image conditions increase the likelihood of error, and there is less opportunity for careful review of potential matches. ICE exacerbates these risks by using the technology in a dangerously lax manner. Even as ICE’s app returns results in an amateurish manner (notably, the app defies standard practices by returning single matches rather than a gallery of potential matches, and does not list confidence ratings), the agency treats matches as definitive identifications. As I wrote previously on Tech Policy Press, this is a shockingly reckless practice, and one that ignores consensus among experts and even law enforcement that using facial recognition this way is unsound and unsafe.
The use of facial recognition as a definitive identification is also incompatible with the most recently published DHS guidelines, which prohibit relying on facial recognition matches as the sole basis for enforcement actions. This means the agency’s rules have either been repealed in secret or are being systemically ignored. Either possibility makes broad, unchecked use of facial recognition—including against protesters and observers—a very real threat.
In fact, reports suggest facial recognition is already being deployed in exactly this manner. The New York Times has documented over half a dozen activists in Minnesota who were subjected to facial recognition scans last month. A DHS official recently told the Financial Times: “I’ve seen the [facial recognition] apps and I don’t like them … It’s rife for abuse. I imagine they’re being used in ways they were not intended.”
Clip from promotion video by NEC, the vendor for CBP and ICE’s Mobile Fortify app, highlighting the company’s facial recognition systems.
Unfortunately, there are currently no laws restricting how ICE, CBP, and other federal law enforcement agencies use facial recognition. While states across the country are increasingly imposing strong limits on the technology, those rules do not apply to federal agencies, and Congress hasn’t passed or taken any action to advance measures to rein in facial recognition surveillance. But growing concerns over ICE misconduct may provide an opportunity for action.
Last month, Rep. Bennie Thompson (D-MS) introduced a bill to block ICE’s use of the Mobile Fortify app in communities. While beneficial, that approach would still leave the door open to other facial recognition systems (for example, ICE also uses Clearview AI). More promisingly, a group of lawmakers led by Senator Ed Markey (D-MA) just introduced a bill that would halt all ICE and CBP use of facial recognition. Given how recklessly ICE is using the technology, hitting pause is a sensible measure.
From a personal standpoint, individuals attending protests who wish to guard against facial recognition may consider wearing a mask or other face covering. But anyone considering this should keep two practical concerns in mind. First, while individuals have the right to remain silent and not answer questions if stopped by ICE officials (the ACLU and NAACP offer helpful explainers on your rights if stopped), refusing to show one’s face or allow a scan may lead an agent to escalate an encounter. Second, a number of states and cities have laws restricting mask-wearing in public. Although such laws are constitutionally suspect, a masked individual may still be forced to deal with a citation or arrest for violating them.
License plates and vehicle surveillance
Another powerful surveillance capability protesters and observers should be cognizant of is vehicle tracking. ICE and CBP have for years operated automated license plate reader (ALPR) systems, networks of cameras and software that automatically scan and log the license plates of all vehicles that pass by. These systems allow the government to easily map vehicle movements across broad areas, and can generate alerts whenever a vehicle on a watchlist is recorded. CBP has even begun to have software flag travel patterns and abnormalities as the basis for car stops.
ICE and CBP vehicle surveillance is powered not only by their own systems, but also by piggybacking off state and local police’s ALPR networks. Over the past year, the ALPR vendor Flock has come under significant scrutiny for facilitating ICE and CBP surveillance and has been forced to backtrack after making false claims about providing federal access to its systems.
Beyond these automated systems, protesters and observers face risks from more discrete vehicle surveillance. In recent months, there have been numerous documented instances of ICE checking individuals’ license plates and then driving to their homes as an intimidation tactic. As reported by Adam Sewer in the Atlantic: “[Judy, an ICE observer] said that ICE agents had taken a picture of her license plate and then later showed up at her house …. [another ICE observer] had told me the same thing—that agents had come to her house, followed her when she left, and then blocked her vehicle and screamed at her to ‘stop fucking following us. This is your last warning.’” In one especially appalling incident in Maine, a masked ICE officer photographed a legal observer's license plate, then told her he was doing so "Because we have a nice little database, and now you're considered a domestic terrorist."
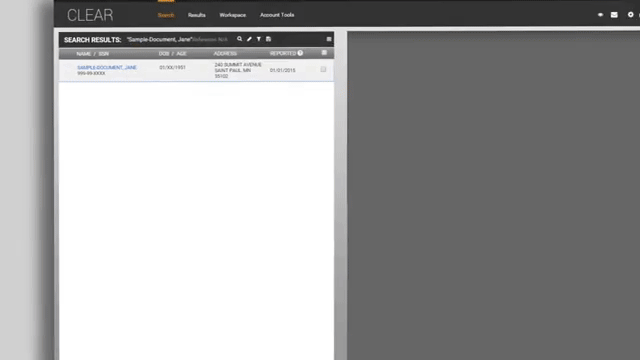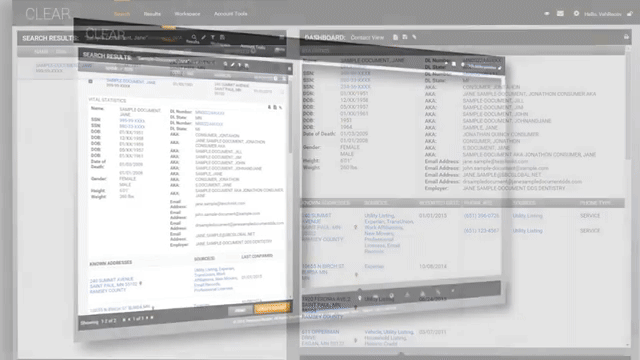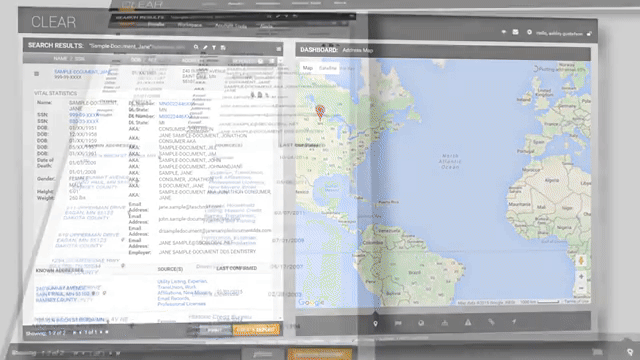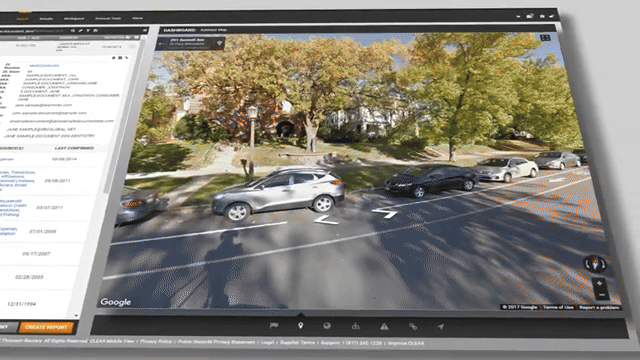
Clip from data broker Thomson Reuters promotional video for its CLEAR product.
ICE’s agents' ability to rapidly look up vehicle information is powered by a mobile app and data vendors. According to a 2021 Privacy Impact Assessment, ICE personnel use a mobile application to “scan license plates whether they are inside or outside their patrol cars …. The vendor software is able to match license plates scanned by ICE personnel with license plates in the vendor’s database.” Through a contract with Thomson Reuters for its “CLEAR” system, ICE is able to take a license plate and access a vast trove of vehicle location and travel data, along with registration and ownership information.
While this is one area with few personal options to protect your privacy (you cannot mask or obscure your license plate), there are policies that could help rein in vehicle surveillance. Closing the Data Broker Loophole would limit unfettered access to vendors' stockpiles of vehicle records.
Important action can also be taken at the state and local level. Shutting down ALPR systems, or at a minimum imposing strict limits on their use, can stop ICE and CBP from co-opting them. In recent months, over a dozen municipalities have suspended Flock systems; last fall, Denver amended its contract with Flock to set a $100,000-per-violation fine for any federal access to its systems.
States should also more vigilantly control access to DMV databases. A recent investigation by Sen. Wyden revealed that ICE has used “Nlets,” a nationwide law enforcement information sharing network, to run hundreds of thousands of queries for DMV data over the past year. More states should follow the example of Illinois, New York, Massachusetts, Minnesota, Oregon, and Washington, which have cut off ICE access to their state DMV data through Nlets.
Stopping improper ICE surveillance is a daunting challenge, but it is not an insurmountable one. By supporting meaningful safeguards and pressing lawmakers to enact smart policy reforms, people can ensure that privacy rights are strong enough to empower individuals and serve as a shield for a democratic society.
Authors
